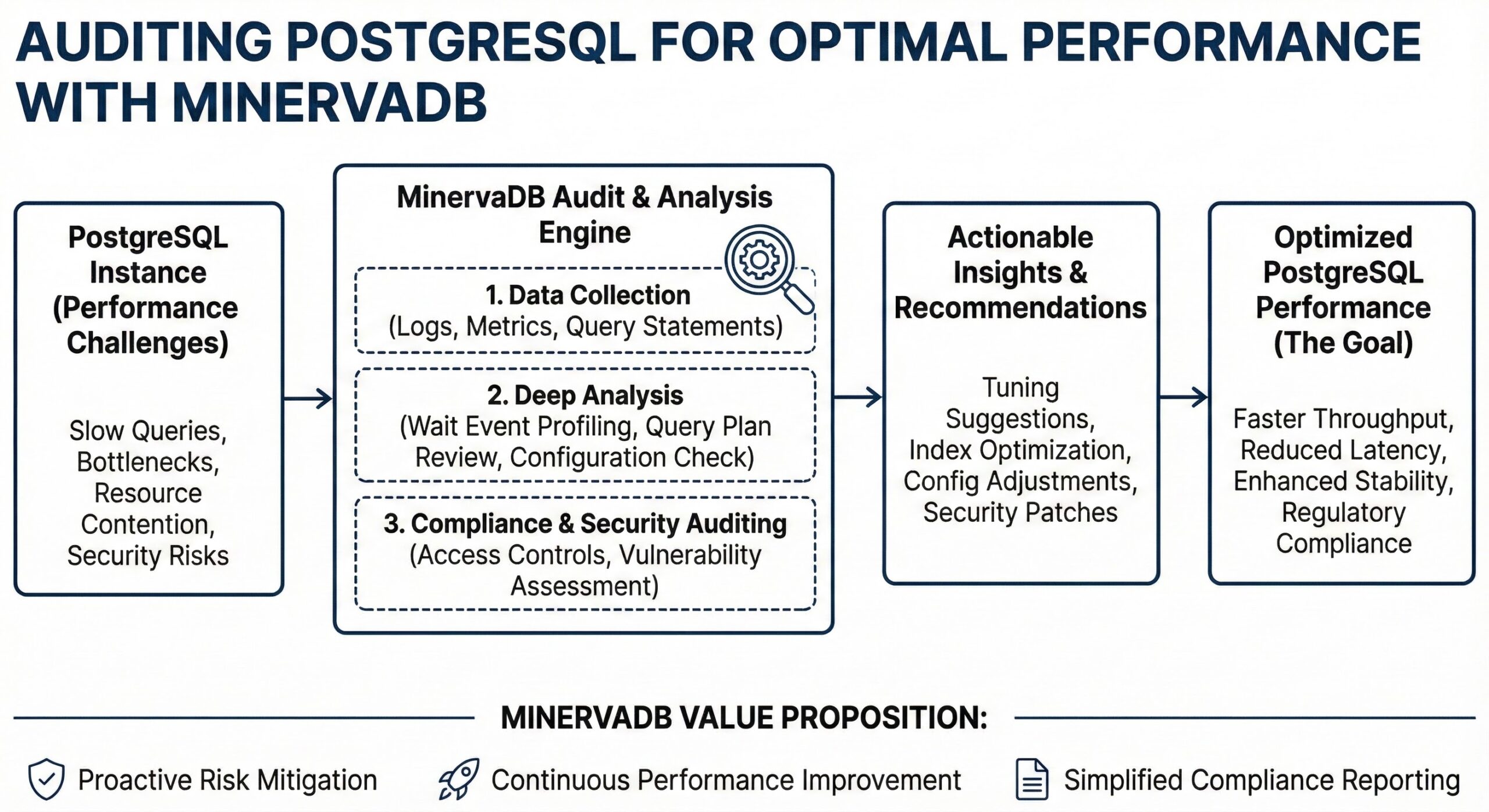
Auditing PostgreSQL for Optimal Performance
Database auditing is a critical component of modern data governance and security strategies. For organizations running PostgreSQL, implementing robust auditing mechanisms ensures compliance with regulatory requirements, enhances security posture, and provides valuable insights into database operations. This guide explores the essential aspects of PostgreSQL auditing and best practices for implementation.
Why PostgreSQL Auditing Matters
Compliance Requirements
Organizations across industries face stringent regulatory requirements such as GDPR, HIPAA, SOX, and PCI-DSS. PostgreSQL auditing helps meet these compliance mandates by:
- Tracking data access and modifications
- Recording user activities and authentication attempts
- Maintaining detailed logs of administrative operations
- Providing audit trails for forensic analysis
Security Enhancement
Auditing serves as both a deterrent and detection mechanism for security threats:
- Identifying unauthorized access attempts
- Detecting suspicious query patterns
- Monitoring privilege escalations
- Tracking data exfiltration attempts
Operational Insights
Beyond compliance and security, auditing provides valuable operational intelligence:
- Performance troubleshooting through query analysis
- Understanding application behavior patterns
- Capacity planning based on usage trends
- Identifying optimization opportunities
PostgreSQL Native Auditing Capabilities
Logging Configuration
PostgreSQL offers extensive logging capabilities through configuration parameters:
Essential Logging Parameters
log_destination: Defines where logs are written (stderr, csvlog, syslog, eventlog)
logging_collector: Enables the logging collector process for capturing stderr output
log_directory: Specifies the directory for log files
log_filename: Sets the naming pattern for log files
log_rotation_age: Determines when to rotate log files based on time
log_rotation_size: Sets the maximum size before log rotation
Connection and Authentication Logging
log_connections: Records all connection attempts
log_disconnections: Logs session terminations
log_hostname: Includes hostname in connection logs
log_line_prefix: Customizes the prefix for each log line with metadata
Statement Logging
PostgreSQL provides granular control over which SQL statements to log:
log_statement: Controls which statements are logged (none, ddl, mod, all)
log_duration: Records the duration of completed statements
log_min_duration_statement: Logs statements exceeding specified execution time
log_checkpoints: Records checkpoint activity
log_lock_waits: Logs long lock waits
Advanced Auditing with pgAudit Extension
Overview
The pgAudit extension enhances PostgreSQL’s native auditing capabilities by providing more detailed and configurable audit logging specifically designed for compliance requirements.
Key Features
Session Audit Logging: Tracks all statements executed in a session
Object Audit Logging: Monitors access to specific database objects
Role-Based Auditing: Applies different audit rules based on user roles
Granular Control: Allows fine-tuned selection of audited operations
Configuration Options
Audit Classes
- READ: SELECT and COPY when source is a relation or query
- WRITE: INSERT, UPDATE, DELETE, TRUNCATE, COPY when destination is a relation
- FUNCTION: Function calls and DO blocks
- ROLE: GRANT, REVOKE, CREATE/ALTER/DROP ROLE
- DDL: All DDL not included in ROLE class
- MISC: Miscellaneous commands like DISCARD, FETCH, CHECKPOINT
Implementation Strategy
Setting up pgAudit involves:
- Installing the extension in the target database
- Configuring audit classes in postgresql.conf or at session level
- Defining object-level audit rules for sensitive tables
- Establishing log rotation and retention policies
- Implementing log analysis and alerting mechanisms
Best Practices for PostgreSQL Auditing
Define Clear Audit Objectives
Before implementing auditing:
- Identify compliance requirements specific to your industry
- Determine which data and operations require auditing
- Establish retention periods for audit logs
- Define roles and responsibilities for audit log management
Balance Security and Performance
Comprehensive auditing can impact database performance:
- Start with critical objects and operations
- Use log_min_duration_statement to focus on slow queries
- Implement log rotation to manage disk space
- Consider asynchronous logging mechanisms
- Monitor system resources after enabling auditing
Secure Audit Logs
Audit logs themselves must be protected:
- Store logs on separate storage from database files
- Implement appropriate file permissions
- Use log shipping to remote secure locations
- Enable log encryption for sensitive environments
- Restrict access to audit logs to authorized personnel only
Regular Review and Analysis
Audit logs provide value only when analyzed:
- Establish regular review schedules
- Implement automated alerting for suspicious activities
- Use log analysis tools for pattern detection
- Create dashboards for audit metrics
- Conduct periodic compliance audits
Audit Log Management
Log Rotation Strategies
Implement effective log rotation to prevent disk space exhaustion:
- Time-based rotation for predictable log volumes
- Size-based rotation for variable workloads
- Combination approaches for optimal management
- Automated archival of rotated logs
Retention Policies
Define retention periods based on:
- Regulatory compliance requirements
- Storage capacity constraints
- Historical analysis needs
- Incident investigation timeframes
Centralized Log Management
For enterprise environments:
- Aggregate logs from multiple PostgreSQL instances
- Implement centralized log storage solutions
- Use SIEM systems for real-time analysis
- Enable correlation across different data sources
Monitoring and Alerting
Key Metrics to Monitor
- Failed authentication attempts
- Privilege escalation events
- DDL operations on production databases
- Unusual query patterns
- Access to sensitive tables outside business hours
Alert Configuration
Establish alerts for:
- Multiple failed login attempts from single source
- Execution of DROP or TRUNCATE commands
- Access by privileged accounts during maintenance windows
- Queries returning large result sets
- Modifications to audit configuration
Common Auditing Challenges
Performance Impact
Extensive logging can affect database performance:
Solution: Implement selective auditing focusing on critical operations and objects
Storage Requirements
Audit logs can consume significant disk space:
Solution: Implement aggressive rotation policies and archive to cost-effective storage
Log Analysis Complexity
Large volumes of audit data can be overwhelming:
Solution: Use automated analysis tools and establish clear review procedures
False Positives
Overly aggressive auditing may generate noise:
Solution: Fine-tune audit rules based on actual usage patterns and risk assessment
PostgreSQL Auditing: A Strategic Approach to Compliance and Database Governance
Effective PostgreSQL auditing requires careful planning, proper implementation, and ongoing management. By leveraging PostgreSQL’s native capabilities and extensions like pgAudit, organizations can build comprehensive audit frameworks that meet compliance requirements while maintaining database performance. Regular review and refinement of audit policies ensure that auditing remains aligned with evolving security threats and business needs.
Implementing robust auditing practices not only satisfies regulatory obligations but also provides valuable insights into database operations, enhances security posture, and supports forensic investigations when needed. As data governance continues to grow in importance, PostgreSQL auditing stands as a fundamental pillar of responsible database management.
About MinervaDB Inc.
MinervaDB Inc. is a premier database consulting and managed services provider specializing in PostgreSQL and other leading database platforms. With years of industry experience and a proven track record of success, our team of certified database experts delivers comprehensive solutions that address the complex challenges facing modern data-driven organizations.
Our core competencies span the entire database lifecycle, from initial architecture design and implementation to ongoing optimization, security hardening, and performance tuning. We understand that each organization has unique requirements, which is why we tailor our services to align with specific business objectives, technical environments, and compliance mandates.
Our Service Offerings Include:
- Database Consulting: Strategic guidance on database architecture, technology selection, migration planning, and best practice implementation
- Managed Database Services: 24/7 monitoring, proactive maintenance, backup management, and incident response for production database environments
- Performance Optimization: Comprehensive performance audits, query tuning, index optimization, and capacity planning to maximize database efficiency
- Security and Compliance: Implementation of robust security frameworks, audit mechanisms, encryption strategies, and compliance solutions for GDPR, HIPAA, SOX, and PCI-DSS
- High Availability Solutions: Design and deployment of replication, clustering, and disaster recovery architectures to ensure business continuity
- Database Migration Services: Seamless migration from legacy systems to PostgreSQL with minimal downtime and risk
At MinervaDB Inc., we pride ourselves on our client-centric approach, combining deep technical expertise with clear communication and transparent project management. Our consultants work closely with your teams to transfer knowledge, build internal capabilities, and ensure long-term success beyond the engagement period.
Whether you’re looking to enhance your existing PostgreSQL infrastructure, migrate from proprietary database systems, or establish enterprise-grade auditing and security practices, MinervaDB Inc. provides the expertise and support needed to achieve your database management goals efficiently and effectively.
Contact us today to learn how we can help optimize your database infrastructure and drive your organization’s data strategy forward.